 Testing IDS solutions has always been a nightmare. Just flooding the box with tons of packets is not the best solution. Today, many firewalls jumped into the “Next Generation” train and propose also deep inspection of the packets up to layer 7 (the application layer). The goal of Tomahawk is to test your security devices using real traffic or attacks replayed from a pcap file. You can replay your own captures but they are on-line repositories of pcap files like pcapr or evilfingers where you can find interesting traces of attacks.
Testing IDS solutions has always been a nightmare. Just flooding the box with tons of packets is not the best solution. Today, many firewalls jumped into the “Next Generation” train and propose also deep inspection of the packets up to layer 7 (the application layer). The goal of Tomahawk is to test your security devices using real traffic or attacks replayed from a pcap file. You can replay your own captures but they are on-line repositories of pcap files like pcapr or evilfingers where you can find interesting traces of attacks.
Tomahawk is designed to test the traffic from end-to-end (See the topology below). Tomahawk runs on a Linux machine with three NICs. Two are used to send (eth0) and receive (eth1) traffic. The third one is used to manage the box.
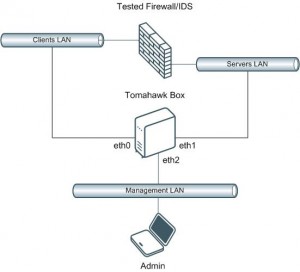
(Click to enlarge)
Tomahawk reads sessions from pcap files. First client’s packet is sent via eth0. If the packet reached eth1, it sends the first server’s packets to eth1, etc. There is a good tutorial on the website. Example of usage: # ./tomahawk -l 3 -a 192.168.0.100 -f http.pcap Completed 1 loop of trace http.pcap Completed 1 loop of trace http.pcap Completed 1 loop of trace http.pcap Finished 3 loops of trace http.pcap Completed: 3, Timed out: 0 Retrans: 0 Sent: 12035 Recv: 12035 # ./tomahawk -l 1 -a 192.168.0.100 -f bad-http.pcap Timeout 1 loop of trace bad-http.pcal Finished 1 loops of trace http.pcap Completed: 0, Timed out: 1 Retrans: 0 Sent: 546 Recv: 546
The flag “-a” allows you to rewrite IP addresses present in the original pcap file to your own addresses. Useful to map traffic to your DMZ or to a specific server. In parallel to security tests, Tomahawk can also be used to perform performance tests. There are useful flags which allows to control how the traffic is generated:
-n maxActive Max number of handlers for a file -l loops Number of times to replay file -R rate playback rate in Mbps (unlimited by default)
