Underground hacker forums are full of complaints from users angry that a developer of some popular banking Trojan or bot program has stopped supporting his product, stranding buyers with buggy botnets. Now, the proprietors of a new ZeuS Trojan variant are marketing their malware as a social network that lets customers file bug reports, suggest and vote on new features in upcoming versions, and track trouble tickets that can be worked on by the developers and fellow users alike.
The ZeuS offshoot, dubbed Citadel and advertised on several members-only hacker forums, is another software-as-a-service malware development. Its target audience? Those frustrated with virus writers who decide that coding their next creation is more lucrative and interesting than supporting current clients.
“Its no secret that the products in our field — without support from the developers — result in a piece of junk on your hard drive. Therefore, the product should be improved according to the wishes of our customers,” Citadel’s developers claim in an online posting. “One problem is that you have probably experienced developers who ignore your instant messages, because there are many customers but there is only one developer.”
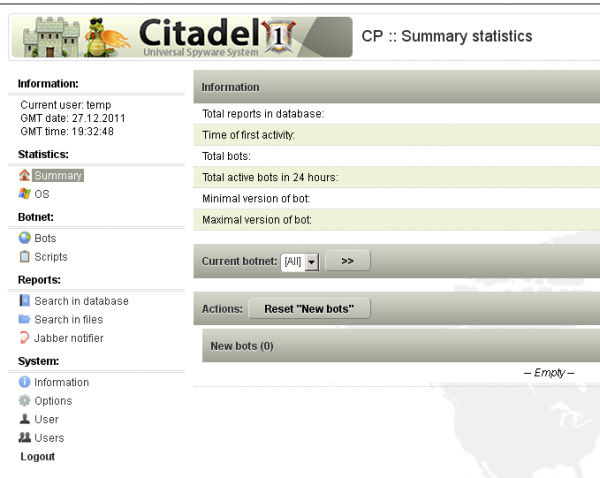
In the following excerpt, taken from a full description of Citadel’s innovations, the developers of this malware strain describe its defining feature as a social networking platform for malware users that is made available through a Web-based portal created by the malware itself.
“We have created for you a special system — call it the social network for our customers. Citadel CRM Store allows you to take part in product development in the following ways:
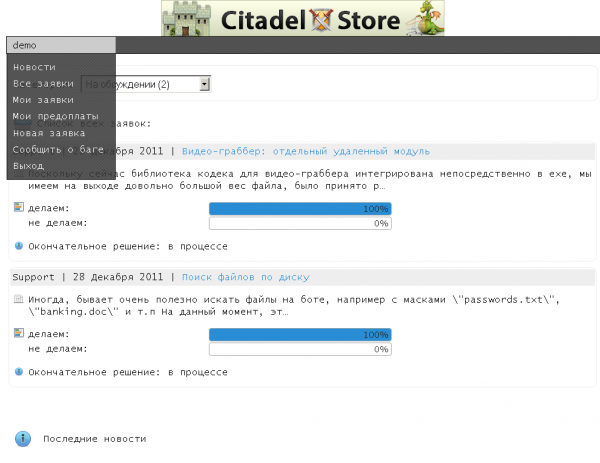
- Report bugs and other errors in software. All tickets are looked at by technical support you will receive a timely response to your questions. No more trying to reach the author via ICQ or Jabber.
-Each client has the right to create an unlimited number of applications within the system. Requests can contain suggestions on a new module or improvements of existing module. Such requests can be public or private.
-Each client has a right to vote on new ideas suggested by other members and offer his/her price for development of the enhancement/module. The decision is made by the developers on whether to go forward with certain enhancement or new module depending on the voting results.
-Each client has the right to comment on any application and talk to any member. Now it is going to be interesting for you to find partners and like-minded people and also to take active parts in discussions with the developers.
- You can see all stages of module development, if it is approved other members. We update the status and time to completion.
- You may pay a deposit, if module is approved (50%). After the deposit is paid by the members, the project starts moving forward, so that the money is paid directly to coders and there will be no laziness or inaction. Everything is clear: every stage of development is thoroughly shown.
-Easy jabber [instant message] notification of new member or developer comments, or the availability of new custom applications.
Citadel may be the first notable progeny of ZeuS since the ZeuS source code was leaked online last year. The authors claim that it includes a number of bug fixes for the most recent ZeuS version, including full support for grabbing credentials from victims using Google Chrome. Also bundled with this update is a component that can record and transmit videos of the victim’s screen activity.
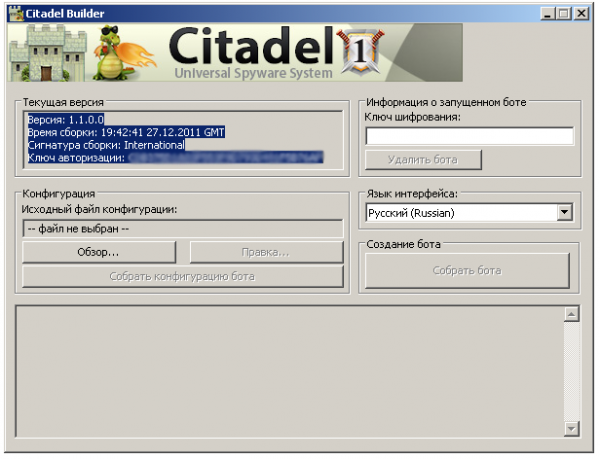
The basic Citadel package — a bot builder and botnet administration panel — retails for $2,399 + a $125 monthly “rent,” but some of its most innovative features are sold as a la carte add-ons. Among those is a $395 software module that allows botmasters to sign up for a service which automatically updates the bot malware to evade the last antivirus signatures. The updates are deployed via a separate Jabber instant message bot, and each update costs an extra $15.
Citadel also boasts a feature that hints at its creator’s location(s). According to the authors, if the malware detects that the victim’s machine is using a Russian or Ukrainian keyboard, it will shut itself down. This feature is almost certainly a hedge to keep the developers out of trouble: Authorities in those regions are far less likely to pursue the Trojan’s creators if there are no local victims.
It will be interesting to see if these malware developers hold true to their word. The growth of a more real-time, user-driven and crowdsourced malicious software market would be a truly disturbing innovation. For now, the miscreants behind Citadel appear upbeat about their chances of ushering in such a reality.
“It’s very interesting for us to work with our clients,” they wrote in an online forum posting. “A lot of authors write in forums that they ‘support the product,’ but at the end the updates only come out once every three months or the author disappears forever. Problem is in author’s motivation. You support us, we support you. It is easy.”